
Intro
You can use DHCP snoopingto help avoid the Denial of Service attacks that result from unauthorized usersadding a DHCP server to the network that then provides invalid configurationdata to other DHCP clients on the network. DHCP snooping accomplishes this by allowing you to distinguish between trustedports (connected to a DHCP server or switch) and untrusted ports connected toend-users. DHCP packets are forwarded between trusted ports without inspection.DHCP packets received on other switch ports are inspected before beingforwarded. Packets from untrusted sources are dropped.
Conditionfor Dropping a PacketTypes
A packet from a DHCP serverreceived on an untrusted port DHCPOFFER,DHCPACK, DHCPNACK
If the switch is configuredwith a list of authorized DHCP DHCPOFFER,DHCPACK, DHCPNACK
server addresses and a packetis received from a DHCP
Dhcp-snooping dhcp-snooping authorized-server 192.168.0.254 dhcp-snooping vlan 1 interface Trk1 dhcp-snooping trust exit The switches are set to trust BOTH the port the authorized dhcp server is attached to and its IP address. Active500EM#show ip dhcp snooping binding all ip dhcp snooping static binding count:1169, dynamic binding count:0 MAC IP address Interface Vlan ID Flag - 00-00-00-00-11-11 192.168.40.1 Ethernet1/0/1 1 S 00-00-00-00-00-10 192.168.40.10 Ethernet1/0/2 1 D 00-00-00-00-00-11 192.168.40.11 Ethernet1/0/4 1 D 00-00-00-00-00-12 192.168.40.12. Hello, I am trying to set DHCP snooping in a network of cisco and hp procurve switches All switches is connected via 802.1q trunk interfaces, Lots of VLANS defined Default VLAN changed to 199 Static-IP clients works, but DHCP clients cannot obtain IP adress Is there any special con.
server on a trusted port witha source IP address that is not
Unless configured to notperform this check, a DHCP packet N/A
received on an untrusted portwhere the DHCP client
hardware address field doesnot match the source MAC
Unless configured to notperform this check, a DHCP packet N/A
containing DHCP relayinformation (option 82) received from
A broadcast packet that has aMAC address in the DHCP DHCPRELEASE,DHCPDECLINE
binding database, but the portin the DHCP binding database
is different from the port onwhich the packet is received
Configuration restrictions andguidelines
When you configure DHCP snooping, follow theserestrictions and guidelines:
·DHCPsnooping operates between the DHCP client and DHCP server, or between the DHCPclient and DHCP relay agent. It does not operate between the DHCP server andDHCP relay agent.
·TheDHCP snooping enabled device cannot act as a DHCP server or DHCP relay agent.
·Thetrusted port and the port connected to the DHCP client must be in the sameVLAN.
·You canconfigure Layer 2 Ethernet interfaces and Layer 2 aggregate interface astrusted interfaces.
·When aLayer 2 Ethernet interface is added to an aggregation group, the DHCP snoopingconfiguration on the interface does not take effect. After the interface isremoved from the aggregation group, the configuration takes effect.
Hp Procurve Dhcp Snooping
HPN Procurve Switches
Enable Globally
dhcp-snooping
Enable Per vlan
dhcp-snoopingvlan 1
dhcp-snoopingvlan 40
Designate authorized servers
dhcp-snoopingauthorized-server 10.15.20.25
dhcp-snoopingauthorized-server 10.9.8.7
Apply to uplink interface to the Core switch
interfaceTrk1
exit
Todisplay the DHCP snooping configuration:
# show dhcp-snooping
DHCP Snooping : Yes
Verify MAC : No
Option 82 Insertion : No
Store lease database : Not configured
----- -----
2 No
.
Hp Procurve Dhcp Snooping Configuration
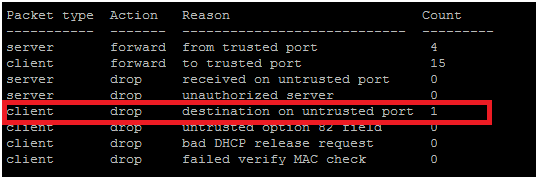
Todisplay statistics about the DHCP snooping process:
Packet type Action Reason Count
----------- ------- -------------------------------------
Client forward to trusted port 8
Server drop unauthorized server 0
Client drop untrusted option 82 field 0
Client drop failed verify MAC check 0

Example HPN Comware 12500 Configuration Procedure
(Derived from 'H3C S12500 DHCP Snooping Configuration Examples' online manual)
ConfigureDHCP Server Switch A
#Enable DHCP.
[SwitchA] dhcp enable
#Configure DHCP address pool 1.
[SwitchA]dhcp server ip-pool 1
[SwitchA-dhcp-pool-1]quit
#Create VLAN 10, specify an IP address for VLAN-interface 10, and add GigabitEthernet 3/0/1to VLAN 10.
[SwitchA]vlan 10
[SwitchA-Vlan-interface10]ip address 10.1.0.2 24
[SwitchA-GigabitEthernet3/0/1]undo shutdown
ConfigureDHCP Snooping Switch B
#Add all ports to VLAN 10. (Details not shown.)
#Enable DHCP snooping.
#Configure GigabitEthernet 3/0/1 as trusted.
[SwitchB-GigabitEthernet3/0/1]dhcp-snooping trust
#Enable ARP detection.
[SwitchB-vlan10]arp detection enable
#Configure GigabitEthernet 3/0/1 as an ARP trusted interface.
[SwitchB]interface GigabitEthernet 3/0/1
Verifyingthe configuration
Afterthe configuration, DHCP clients can obtain IP addresses only from theauthorized DHCP server (Switch A).
# Display information about trusted ports.
<SwitchB>display dhcp-snooping trust
DHCPSnooping trust becomes active.
TheDHCP snooping device checks the validity of ARP packets received onGigabitEthernet 3/0/2 and GigabitEthernet 3/0/3, and then performs uservalidity check based on DHCP snooping entries.
# Display all ARP detection-enabled VLANs.
<SwitchB>display arp detection
10
# Display DHCP snooping entries.
<SwitchB>display dhcp-snooping
Theclient binding table for all untrusted ports.
TypeIP Address MAC Address Lease VLAN SVLAN Interface
D 10.1.0.3 0000-0101-010b 85999 10 N/A GigabitEthernet3/0/2
---1 dhcp-snooping item(s) found ---




